
Table of Contents
ABSTRACT
Ai based threat detection plays a crucial role in securing modern cloud computing environments, which are widely used for deploying scalable and cost-efficient applications. Despite their advantages, cloud platforms face serious cybersecurity challenges due to their dynamic and distributed nature. Traditional security mechanisms such as signature-based intrusion detection systems and static firewalls are mostly reactive and ineffective against advanced cyberattacks, including Distributed Denial of Service (DDoS) attacks, brute-force intrusions, and zero-day exploits.
Ai based threat detection leverages Artificial Intelligence and Machine Learning techniques to analyze complex network traffic patterns and identify malicious activities in real time. This project focuses on designing and evaluating an Ai based threat detection system using the CloudSim simulation framework, enabling realistic, controlled, and cost-effective analysis of cloud network behavior. The proposed system implements two independent detection interfaces to facilitate comparative evaluation of different feature sets and machine learning models.
Ai based threat detection processes cloud traffic data to accurately classify normal and malicious activities while minimizing false positives. CloudSim is utilized to simulate cloud infrastructures, virtual machines, and workloads, ensuring scalability and flexibility during experimentation. The results demonstrate that Ai based threat detection enhances adaptability, accuracy, and reliability in identifying cloud-based cyber threats. The study further emphasizes the importance of simulation-driven validation in strengthening cloud security and advancing intelligent threat detection research.
INTRODUCTION
Overview
Cloud computing has become a dominant paradigm for delivering scalable, on-demand, and cost-efficient computing resources. Organizations increasingly depend on cloud infrastructures to host mission-critical applications, process large volumes of data, and deliver digital services. However, the distributed nature of cloud environments—combined with virtualization, multi-tenancy, and dynamic resource provisioning—introduces complex cybersecurity challenges that demand advanced security solutions.
Cyber threats such as Distributed Denial of Service (DDoS) attacks, brute-force intrusions, botnets, insider threats, and web-based attacks continue to increase in sophistication and frequency. Traditional security mechanisms, including static firewalls and signature-based intrusion detection systems, are largely reactive and ineffective against rapidly evolving attack patterns. These conventional approaches struggle to adapt to unknown threats and often result in high false-positive rates, reducing overall detection reliability.
Ai based threat detection offers an intelligent and adaptive approach by leveraging Artificial Intelligence and Machine Learning techniques to automatically learn patterns from historical and real-time cloud traffic data. By identifying anomalies and malicious behavior proactively, Ai based threat detection improves accuracy and responsiveness in cloud security operations. Furthermore, integrating Ai based threat detection with cloud simulation platforms such as CloudSim enables realistic evaluation of security models without deploying physical cloud infrastructure. This project focuses on implementing and analyzing Ai based threat detection using CloudSim through multiple detection interfaces, allowing comparative analysis of different feature sets and learning models for enhanced cloud security.
Introduction to Domain
The project domain integrates Cloud Computing, Cybersecurity, and Artificial Intelligence to address modern cloud security challenges. Cloud computing provides flexibility, scalability, and efficient resource utilization, but it also expands the attack surface due to virtualization, shared resources, and dynamic provisioning. Cybersecurity focuses on safeguarding cloud infrastructure, data, and applications from malicious activities, while Artificial Intelligence strengthens this protection through intelligent, adaptive, and automated security mechanisms. Ai based threat detection plays a key role in identifying complex and evolving cyber threats within cloud environments.
CloudSim serves as a simulation framework for modeling cloud components such as data centers, virtual machines (VMs), brokers, and workloads. By simulating cloud traffic and operational scenarios, CloudSim enables researchers to evaluate security algorithms under controlled, repeatable, and risk-free conditions. Integrating CloudSim with Ai based threat detection allows effective analysis of attack behaviors and system responses without the need for real-world cloud deployment.
Overview
Ai based threat detection systems monitor cloud network traffic and virtual machine (VM) behavior by applying statistical analysis and machine learning techniques. These systems learn normal operational patterns within cloud environments and identify deviations that may indicate malicious activities or cyberattacks. By enabling intelligent and automated analysis, Ai based threat detection enhances the accuracy and responsiveness of cloud security mechanisms.
The proposed project implements Ai based threat detection through two independent detection interfaces designed for effective analysis and comparison:
- Detection Page 1: Multi-class classification of cloud network threats using comprehensive flow-level features to identify different attack types.
- Detection Page 2: Simplified or binary threat detection using alternative feature sets and scaling techniques for efficient and rapid classification.
This modular architecture improves flexibility, supports experimentation, and enables comparative evaluation of multiple Ai based threat detection models within simulated cloud environments, contributing to more robust and adaptable cloud security solutions.
Machine Learning Task
The machine learning task in this project is formulated as a supervised classification problem within the scope of Ai based threat detection. Network traffic records are analyzed and classified into multiple categories, including benign traffic and specific cyberattack types such as Distributed Denial of Service (DDoS), port scanning, brute-force attacks, bot activities, and web-based intrusions. The core machine learning pipeline for Ai based threat detection consists of feature extraction, data normalization, model training, and threat prediction.
Supervised learning models used in Ai based threat detection learn complex behavioral patterns from labeled datasets, enabling accurate identification of both known attacks and previously unseen malicious activities. The system supports real-time prediction through manual data input as well as batch-based analysis using CSV file uploads, ensuring flexibility and scalability in practical cloud security scenarios.
History and Relationships to Other Fields
Machine learning emerged from early artificial intelligence research aimed at enabling systems to learn from data rather than relying solely on explicit programming. Over time, machine learning has developed strong relationships with related disciplines such as data mining, statistics, optimization, and cybersecurity. This evolution has laid the foundation for advanced security applications, including Ai based threat detection, which relies on intelligent data-driven analysis.
In cloud security, machine learning techniques are widely applied in intrusion detection, anomaly detection, malware classification, and network traffic analysis. The integration of machine learning with cloud computing has enabled scalable, automated, and intelligent security frameworks. Within this context, Ai based threat detection represents a key convergence point, combining analytical intelligence with cloud scalability to enhance the identification and mitigation of complex cyber threats.
Relation to Data Mining
Data mining focuses on discovering meaningful patterns and insights from large-scale datasets. In cloud security environments, data mining techniques are applied to analyze system logs, network traffic flows, and user behavior patterns. These analytical processes form a critical foundation for Ai based threat detection, enabling effective interpretation of complex and high-dimensional cloud data.
Key data mining steps such as feature selection, dimensionality reduction, and noise removal significantly enhance machine learning performance. The proposed system incorporates comprehensive data preprocessing and feature selection methods to improve model efficiency and accuracy. By strengthening data quality and relevance, Ai based threat detection models achieve more reliable classification and improved detection of malicious activities in cloud environments.
Relation to Optimization
Optimization techniques play a vital role in enhancing model accuracy, computational efficiency, and overall resource utilization. In the context of Ai based threat detection, optimization algorithms are used during the training phase to minimize error functions and improve the learning capability of machine learning models. Effective optimization ensures that models converge faster and achieve higher detection accuracy.
Within cloud environments, optimization is equally important for reducing computational overhead and ensuring timely analysis of large-scale network traffic data. By applying efficient optimization strategies, Ai based threat detection systems can deliver faster and more reliable threat identification while maintaining scalability and performance in dynamic cloud infrastructures.
Relation to Statistics
Statistics forms the mathematical foundation of machine learning and plays a critical role in analyzing and interpreting data patterns. In Ai based threat detection, statistical concepts such as probability distributions, correlation analysis, variance, and hypothesis testing are applied to understand normal and abnormal network traffic behavior within cloud environments. These statistical techniques support effective feature analysis and anomaly identification.
Statistical evaluation metrics are also essential for assessing the performance of security models. Measures such as accuracy, precision, recall, and F1-score are widely used to evaluate the effectiveness of Ai based threat detection systems, ensuring reliable, consistent, and measurable performance in identifying cyber threats.
Problem Statement
The rapid adoption of cloud computing has transformed modern information technology infrastructures by enabling scalability, flexibility, and cost efficiency. However, this transformation has also introduced complex security challenges arising from virtualization, multi-tenancy, dynamic resource provisioning, and geographically distributed cloud environments. Cloud networks are continuously exposed to sophisticated cyber threats such as Distributed Denial of Service (DDoS) attacks, brute-force intrusions, botnet activities, insider misuse, and advanced persistent threats. In this context, Ai based threat detection has become essential for identifying and mitigating malicious activities in real time within dynamic cloud ecosystems.
Traditional cloud security solutions, including firewalls and signature-based intrusion detection systems, are largely reactive and rely on predefined rules and known attack signatures. As a result, these systems are ineffective against zero-day attacks and rapidly evolving threat patterns. Furthermore, conventional approaches often generate a high number of false positives, overwhelming security administrators and delaying timely responses. The lack of adaptability and intelligence in such mechanisms significantly limits their effectiveness in cloud environments where traffic behavior and workloads change frequently, underscoring the need for Ai based threat detection solutions.
Although Artificial Intelligence and Machine Learning techniques have demonstrated promising improvements in detection accuracy, many existing AI-driven security systems suffer from notable limitations. Several approaches are evaluated in isolated or real-world settings without controlled experimentation, making performance assessment complex and costly. Additionally, many solutions adopt a single detection strategy and lack modular or comparative detection mechanisms. The absence of cloud-specific simulation platforms, such as CloudSim, further restricts systematic evaluation of Ai based threat detection under diverse cloud configurations and workload conditions.
Therefore, there is a critical need for an intelligent, scalable, and cloud-aware security solution that can adapt to evolving cyber threats while minimizing false alarms. The problem addressed in this project is the design and implementation of an Ai based threat detection system using the CloudSim simulation framework. The proposed approach aims to accurately identify malicious cloud network activities, support multiple detection interfaces for comparative analysis, reduce false positives, and enhance overall cloud security through adaptive and intelligent analysis. By enabling effective evaluation of AI models in simulated cloud environments, Ai based threat detection contributes to improved resilience, reliability, and trustworthiness of cloud infrastructures.
System Analysis
Ai based threat detection is implemented in the system through a structured processing pipeline that analyzes user-submitted data to assess security and authenticity. The system follows multiple stages, including data pre-processing, feature extraction, model inference, and result visualization. The backend, developed using Flask, manages the core analytical and detection processes required for Ai based threat detection, while the frontend, built with React, provides an intuitive interface for users to submit inputs and view detailed analysis results. This architecture ensures efficient processing, scalability, and user-friendly interaction.
Proposed System
The proposed system is an Ai based threat detection solution designed and evaluated using the CloudSim simulation framework to enhance security in cloud computing environments. The system focuses on identifying malicious network activities by analyzing cloud traffic patterns and virtual machine (VM) behavior using machine learning techniques. Unlike traditional security mechanisms that depend on static rules and predefined signatures, Ai based threat detection adopts an intelligent and adaptive approach capable of detecting both known and previously unseen cyber threats.
CloudSim is utilized to model essential cloud infrastructure components such as data centers, virtual machines, brokers, and workloads. This simulation-based approach enables controlled experimentation across diverse cloud configurations without the need for real-world deployment. By integrating simulated cloud traffic with Ai based threat detection modules, the system allows realistic and repeatable evaluation of detection performance.
A key feature of the proposed system is the implementation of two independent detection interfaces within the Ai based threat detection framework. Each interface employs a distinct feature set or machine learning model, enabling comparative analysis of detection accuracy, response behavior, and false-positive rates. This modular design enhances flexibility, scalability, and extensibility. Additionally, detected threats are systematically logged for monitoring and administrative review, further strengthening visibility and security management in cloud environments.
Objectives
The primary objective of the proposed system is to design and implement an intelligent security solution that strengthens cloud protection through adaptive and data-driven analysis. The system is centered on Ai based threat detection to effectively identify, analyze, and mitigate cyber threats in dynamic cloud environments. The specific objectives of the proposed system are as follows:
- To design and develop an Ai based threat detection system capable of accurately identifying malicious activities in cloud network traffic.
- To utilize the CloudSim simulation framework for modeling cloud environments and evaluating Ai based threat detection mechanisms in a controlled, scalable, and cost-effective manner.
- To implement and evaluate multiple machine learning models for efficient threat classification and analysis.
- To support two independent detection interfaces to enable comparative evaluation of Ai based threat detection models and feature sets.
- To reduce false-positive rates while maintaining high detection accuracy in cloud security monitoring.
- To provide efficient logging, visualization, and reporting of detected threats for administrative analysis and decision-making.
- To enhance the adaptability of Ai based threat detection mechanisms to evolving and previously unseen cyber-attack patterns.
Motivation
The motivation for this project stems from the increasing reliance on cloud computing and the rising sophistication of cyber threats targeting cloud infrastructures. Traditional security mechanisms are largely reactive, require frequent manual updates, and fail to effectively detect zero-day attacks and rapidly evolving threat patterns. Additionally, cloud environments introduce further security challenges due to virtualization, multi-tenancy, and frequent workload variations, increasing the need for intelligent security solutions such as Ai based threat detection.
Although Artificial Intelligence and Machine Learning techniques have shown significant potential in enhancing cybersecurity, many existing solutions lack cloud-specific evaluation and operational flexibility. Most approaches are tested in isolated or static environments and do not incorporate simulation-based validation, leading to a gap between theoretical effectiveness and real-world deployment. This limitation reduces the practical applicability of many intelligent security models, particularly in dynamic cloud settings.
The core motivation of this project is to address these challenges by integrating Ai based threat detection with the CloudSim simulation framework. By adopting a simulation-driven, modular, and intelligent detection approach, the project aims to advance cloud security research, reduce deployment and testing costs, and enable systematic evaluation of AI models under diverse cloud configurations. Ultimately, Ai based threat detection supports the development of more adaptable, reliable, and scalable security solutions for modern cloud environments.
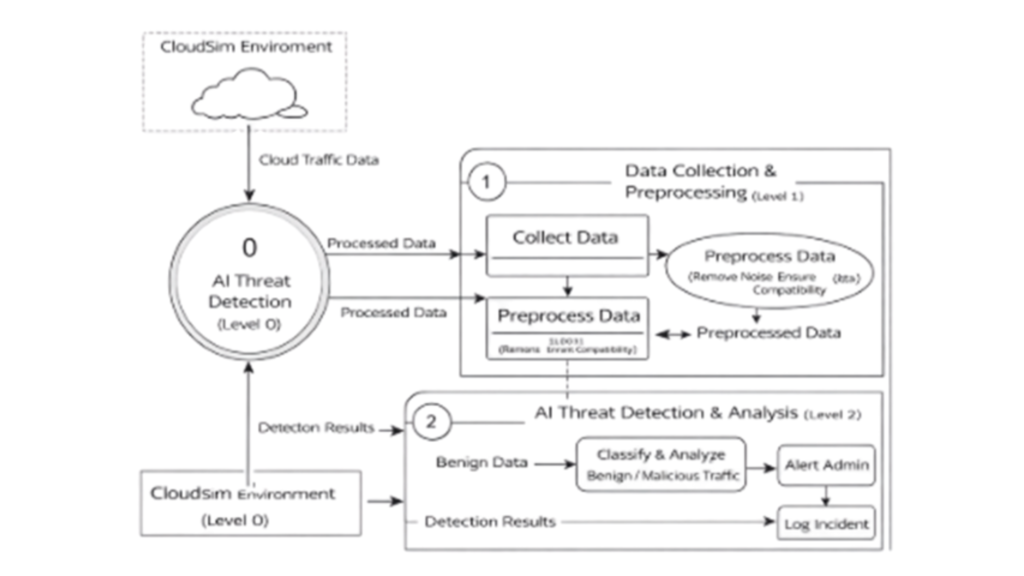
Data Flow Diagram (DFD)
The Data Flow Diagram (DFD) depicts the movement of data within the proposed Ai based threat detection system, illustrating how input data is processed to generate actionable security outputs. It provides a clear view of interactions between cloud simulation, AI analysis, and reporting components.
In the proposed system, data originates from cloud network traffic and virtual machine activity generated within the CloudSim simulation environment. This raw data is collected and preprocessed to remove noise, normalize features, and ensure compatibility with machine learning models. The cleaned and structured data is then fed into the Ai based threat detection module for classification and threat analysis.
When malicious activity is detected, the system generates real-time alerts and logs the incidents for administrative review and monitoring. Traffic identified as benign is stored for future reference, model retraining, and continuous improvement. The DFD highlights the seamless flow of data from cloud simulation to intelligent analysis and reporting, emphasizing the functionality, transparency, and effectiveness of Ai based threat detection in securing cloud environments.
SYSTEM REQUIREMENTS AND SPECIFICATION
Introduction to System Requirements Specification (SRS)
Software Requirements Specification (SRS) is a comprehensive and structured document that formally defines both the functional and non-functional requirements of a software system. It serves as a central reference for all stakeholders, including developers, designers, testers, and end users, ensuring a shared understanding of system objectives and operational constraints. By clearly specifying system behavior, inputs, outputs, and performance criteria, the SRS reduces misinterpretations and establishes a solid foundation for the software development life cycle.
In the context of the proposed Ai based threat detection system using CloudSim, the SRS outlines operational objectives, architectural expectations, and technical limitations. It defines how the system should simulate cloud environments, process cloud network traffic, apply machine learning models for threat detection, and generate results under varying conditions. Additionally, the SRS specifies the necessary resources for execution, including hardware capacity, software tools, and supporting libraries, ensuring efficient and reliable operation within the CloudSim framework.
The SRS also emphasizes key quality attributes such as performance, scalability, security, accuracy, and usability. Given the dynamic nature of cloud environments, the proposed system must adapt to fluctuating workloads and evolving cyber threats while maintaining high detection accuracy and minimal false positives. These expectations are explicitly documented to guide the design of modular, scalable, and maintainable components that align with cloud security requirements.
By systematically documenting requirements, the SRS helps prevent scope creep, reduces development risks, and facilitates effective testing and validation. It provides a benchmark to evaluate the implemented system’s compliance with original objectives. In this project, the SRS serves as a guiding document to ensure that the Ai based threat detection system meets the required standards of security, performance, and usability, enabling reliable and intelligent threat detection in cloud environments.
Functional Requirements
Functional requirements define the specific actions and services that the system must perform, forming the core capabilities of the proposed Ai based threat detection system. The functional requirements are as follows:
- The system shall simulate a cloud environment using CloudSim, including virtual machines, brokers, and workloads.
- The system shall collect and process network traffic and virtual machine activity data generated within the CloudSim environment.
- The system shall support both manual input and file-based input (CSV) for threat detection analysis.
- The system shall preprocess input data by handling missing values, normalization, and feature selection.
- The system shall implement machine learning models to classify cloud traffic as benign or malicious.
- The system shall support two independent threat detection interfaces for comparative evaluation of Ai based threat detection models and feature sets.
- The system shall clearly display prediction results to the user.
- The system shall log detected threats along with relevant metadata, including IP address, attack type, and timestamp.
- The system shall provide administrative access for monitoring and managing detected threats.
- The system shall restrict access to authorized users through secure authentication mechanisms.
- The system shall allow blocking of malicious IP addresses based on detected threats.
- The system shall ensure secure storage of threat logs, results, and system data.
Non-Functional Requirements
Non-functional requirements specify the quality attributes of the system, ensuring efficient, reliable, and secure operation of the Ai based threat detection system within a cloud simulation environment. Key non-functional requirements include:
- Performance: The system shall detect threats with minimal latency and provide timely results.
- Scalability: The system shall handle increasing volumes of simulated cloud traffic without performance degradation.
- Reliability: The system shall operate consistently and accurately during repeated simulations.
- Security: User data, system logs, and detection results shall be protected from unauthorized access.
- Usability: The user interface shall be simple and intuitive for both administrators and users.
- Maintainability: The system shall be modular and easy to update with new machine learning models or features.
- Portability: The system shall run on different platforms with minimal configuration changes.
- Accuracy: The system shall achieve high detection accuracy while minimizing false positives.
- Availability: The system shall be accessible and operational whenever required during simulation and testing.
Hardware Requirements
The hardware requirements specify the minimum system configuration needed to execute the proposed system efficiently.
- Processor: Intel Core i5 (3.0 GHz) or higher
- RAM: Minimum 16 GB
- System Type: 64-bit Operating System
- Hard Disk: 500 GB or higher
- Display: Standard monitor with minimum 1366×768 resolution
Adequate hardware resources are essential to support CloudSim simulations, machine learning model execution, and data processing tasks.
Software Requirements
The software requirements specify the platforms, tools, and libraries required for system development and execution.
- Operating System: Windows 11
- Programming Languages: Python, Java
- Simulation Tool: CloudSim
- Development Environment:
- Anaconda Navigator
- Jupyter Notebook
- Eclipse IDE
- Python Libraries:
- NumPy
- Pandas
- Scikit-learn
- Matplotlib
- Seaborn
- Joblib
- Web Framework (if applicable): Flask
- Database: MySQL
- Version Control (optional): Git
These tools and libraries enable efficient development, simulation, data analysis, and deployment of the threat detection system.
Introduction to Python
Python is a widely used, high-level, general-purpose programming language created by Guido van Rossum in 1991 and further developed by the Python Software Foundation. Designed with an emphasis on code readability, Python’s syntax allows programmers to express concepts in fewer lines of code, making it ideal for rapid development and system integration. In the context of Ai based threat detection, Python provides the flexibility and extensive libraries required for implementing machine learning models, data preprocessing, and cloud simulation integration.
There are two major versions of Python: Python 2 and Python 3, which differ significantly in syntax and features.
- Finding an Interpreter:
- Windows: Free interpreters such as IDLE, bundled with Python downloads from python.org, can be used to run Python scripts.
- Linux: Python is typically preinstalled on popular distributions such as Ubuntu and Fedora. The version can be verified by typing
pythonin the terminal emulator. - macOS: macOS usually comes with Python 2.7. Python 3 must be manually installed from python.org.
- Importance of Python:
Python is high-level, interpreted, interactive, and object-oriented, offering several advantages for projects like Ai based threat detection:- Interpreted: Each line is executed at runtime, eliminating the need for compilation.
- Interactive: Developers can write and test code in real-time via the Python prompt.
- Object-Oriented: Supports encapsulation and modular programming using objects, aiding maintainability and code organization.
- Beginner-Friendly: Python is accessible for beginners while supporting complex applications, from text processing to web applications and games.
- Easy to Maintain: Python’s readability and English-like syntax simplify code maintenance.
- Broad Standard Library: Offers an extensive collection of libraries and frameworks, useful for AI, data processing, and cloud simulations.
- Portable: Python runs on Windows, Linux, macOS, Raspberry Pi, Android, and other platforms with consistent behavior.
- Extendable: Low-level modules can be added to customize Python functionality using tools like PIP.
- Database Support: Provides interfaces for both SQL and NoSQL databases, including MySQL, MongoDB, and PostgreSQL, enabling data storage and retrieval for Ai based threat detection applications.
By leveraging Python, the Ai based threat detection system benefits from rapid development, modular design, cross-platform compatibility, and access to powerful machine learning and cloud simulation libraries, making it an ideal choice for implementing intelligent threat detection solutions in cloud environments.
System Architecture
The system architecture of the proposed solution is designed using a layered approach, where each layer performs specific functions while interacting seamlessly with adjacent layers. This structure enhances modularity, maintainability, and extensibility, enabling effective implementation of Ai based threat detection in cloud environments.
Cloud Simulation Layer
This foundational layer is implemented using CloudSim and simulates essential cloud infrastructure components such as data centers, virtual machines (VMs), brokers, and task scheduling mechanisms. It generates realistic cloud workloads and network behaviors under various configurations. By allowing experimentation with different VM capacities, task loads, and resource allocation policies, this layer provides a controlled environment for evaluating Ai based threat detection mechanisms.
Data Collection and Preprocessing Layer
This layer handles data generated by CloudSim or uploaded via external sources. Raw data may contain inconsistencies, missing values, and redundant features that can negatively impact model performance. The preprocessing tasks performed in this layer—such as data cleaning, normalization, feature selection, and transformation—ensure high-quality input for Ai based threat detection models, improving accuracy and reliability.
AI Threat Detection Layer
At the core of the system, this layer hosts multiple machine learning models for detecting malicious activities in cloud network traffic. Depending on the selected detection interface, different feature sets and models are applied. The layer is extensible, allowing new models to be integrated without altering the overall system structure. Predictions generated by this layer classify traffic as benign or malicious and, in some cases, identify specific attack types, forming the intelligence behind Ai based threat detection.
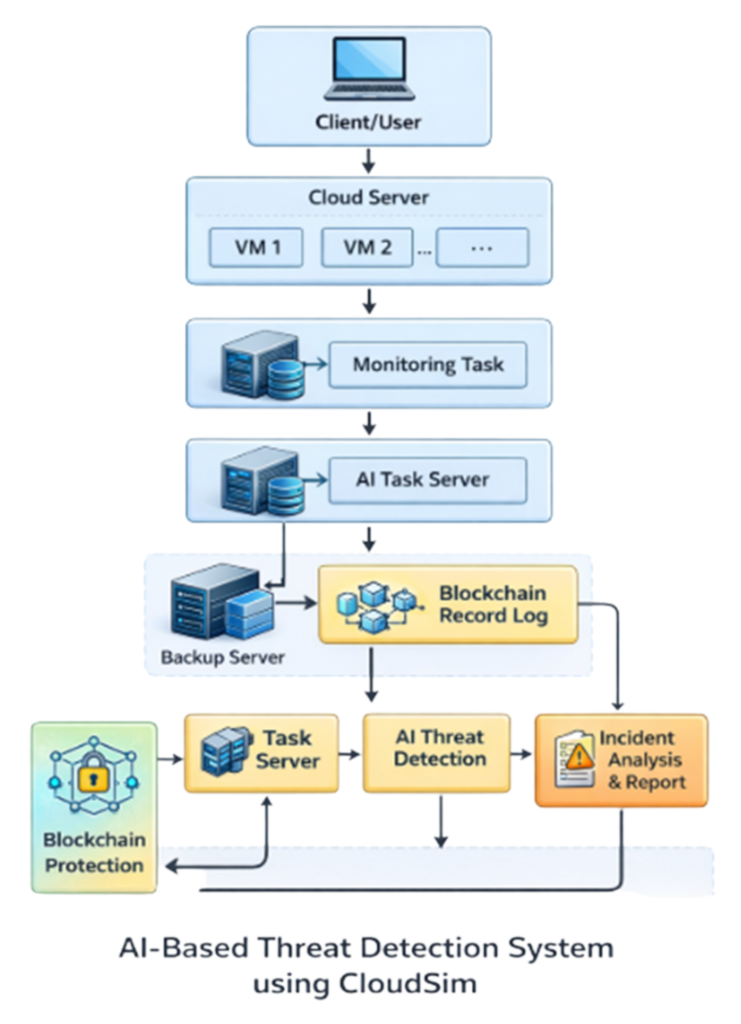
Application and Presentation Layer
The topmost layer provides user interaction and result visualization. Users can submit inputs, initiate threat detection, and view predictions, while administrative users can monitor detected threats, analyze logs, and evaluate system performance. This layer ensures usability and transparency by presenting complex analytical results in a clear, understandable format, supporting informed decision-making based on Ai based threat detection outputs.
The layered architecture ensures separation of concerns, reduces system complexity, and allows independent modification of individual components, providing a robust and flexible framework for implementing Ai based threat detection in cloud computing environments.



