
Table of Contents
INTRODUCTION
OVERVIEW
AI based intrusion detection system technologies are increasingly vital as the Industrial Internet of Things (IIoT) becomes deeply integrated into everyday life and industrial operations. This rapidly emerging paradigm is transforming modern cities into smart cities, while industries across the globe are adopting connected devices at an unprecedented scale. A study conducted in 2021 highlighted this growth, reporting 8.6 billion connected IoT devices in 2019, increasing to 9.76 billion in 2020 and 11.28 billion in 2021. Furthermore, projections estimate nearly 29.42 billion connected devices by 2030. Through advanced communication technologies, IIoT enables the deployment of billions of interconnected devices supporting applications in agriculture, healthcare, manufacturing, and transportation. These systems promise enhanced efficiency, automation, and productivity through intelligent and remote management.
Despite these advantages, the IIoT ecosystem faces severe security challenges. Continuous connectivity, extensive data exchange, and resource-constrained device architectures significantly increase exposure to cyber threats. As a result, protecting IIoT infrastructures has become a critical concern, making the AI based intrusion detection system an essential component of modern cybersecurity strategies. Intrusion Detection Systems (IDSs) serve as a proactive defense layer by monitoring system and network activities for malicious behavior that may bypass traditional security mechanisms. IDSs provide early alerts, enabling timely responses that reduce potential damage and preserve system integrity.
Beyond conventional IDS approaches, several complementary security mechanisms have been proposed to enhance IIoT protection. For instance, cryptographic schemes have been developed to ensure secure data encryption and authentication without relying on traditional certificates, while other methods verify device legitimacy using secret keys and random values instead of passwords. Although effective, these solutions alone are insufficient against evolving and sophisticated cyber attacks, reinforcing the importance of an AI based intrusion detection system tailored to IIoT environments.
Existing IDS solutions for IIoT often struggle with accurate anomaly detection, leading to high false alarm rates, reduced detection accuracy, and performance degradation. These shortcomings highlight the need for more advanced and adaptive techniques. Intelligent IDS solutions leveraging artificial intelligence have therefore gained significant attention. In particular, machine learning approaches enable attack classification without explicit knowledge of attack signatures. However, traditional ML models lack the complexity needed to capture intricate attack patterns, limiting their effectiveness compared to an AI based intrusion detection system built on deep learning.
Deep learning (DL) models, such as convolutional neural networks (CNNs), simulate human cognitive processes through multilayer architectures, enabling them to learn complex feature representations. DL-driven IDS frameworks can effectively identify and predict diverse IIoT attacks, offering superior detection rates and reliability. Consequently, an AI based intrusion detection system using DL techniques is considered a powerful defense mechanism for IIoT networks.
Nevertheless, DL models are often criticized as black-box systems, providing predictions without clear explanations. This lack of transparency reduces trust and limits practical adoption. To overcome this limitation, explainable artificial intelligence (XAI) has emerged as a promising solution. By integrating XAI methods, an AI based intrusion detection system can provide interpretable insights into its decision-making process, enabling cybersecurity professionals to understand, trust, and refine the model outputs.
This research introduces a novel framework that integrates deep learning with XAI for both binary and multi-class classification. The proposed AI based intrusion detection system employs an ensemble architecture combining three CNN models with an Extreme Learning Machine (ELM) to enhance security in IIoT networks. The framework is evaluated using the TON_IoT dataset, demonstrating improved performance over existing state-of-the-art IDS solutions. Furthermore, interpretability is enhanced through LIME and SHAP techniques, allowing transparent explanations of predictions. By improving accuracy, transparency, and reliability, this AI based intrusion detection system aims to strengthen IIoT defenses and effectively mitigate cyber threats.
MOTIVATION
The motivation behind this project arises from the increasing need to secure Industrial Internet of Things (IIoT) systems through AI based intrusion detection mechanisms. As IIoT devices are widely deployed across industries such as manufacturing, healthcare, transportation, and energy, the attack surface of these interconnected systems has expanded significantly, making them attractive targets for cyber threats.
Conventional security approaches are often inadequate in detecting complex and evolving attacks within IIoT environments. In this context, AI based intrusion detection systems play a vital role by continuously monitoring network traffic and identifying abnormal or malicious activities in real time. These intelligent systems have the potential to enhance threat detection accuracy compared to traditional rule-based methods.
However, many existing intrusion detection solutions, especially those relying on deep learning models, suffer from limitations such as high false-positive rates and poor interpretability. The lack of transparency in AI based intrusion detection decisions makes it challenging for cybersecurity professionals to understand why a particular activity is classified as malicious, reducing trust and practical usability.
The core motivation of this project is to overcome these challenges by integrating deep learning–driven AI based intrusion detection with Explainable Artificial Intelligence (XAI) techniques. This integration aims to improve the clarity, reliability, and effectiveness of intrusion detection decisions, enabling security experts to analyze, validate, and refine the system’s outputs.
Additionally, the use of the ToN-IoT dataset ensures realistic evaluation under diverse and modern attack scenarios. Overall, this project is motivated by the goal of developing a transparent, accurate, and robust AI based intrusion detection framework to strengthen IIoT security and protect critical infrastructure from cyber threats.
OBJECTIVE
• Develop a robust AI based intrusion detection system specifically designed for Industrial Internet of Things (IIoT) networks to effectively address their complex and dynamic security challenges.
• Utilize the ToN-IoT dataset, which represents diverse real-world IIoT environments, to ensure the proposed AI based intrusion detection framework can handle evolving and sophisticated cyberattack scenarios.
• Achieve high detection accuracy exceeding 99% by integrating advanced deep learning techniques, including Convolutional Neural Networks (CNNs), along with a novel ensemble-based classification strategy.
• Improve the transparency and interpretability of the intrusion detection process by incorporating Explainable Artificial Intelligence (XAI) techniques such as SHAP and LIME, enabling stakeholders to clearly understand the decision-making behavior of the AI based intrusion detection model and the relevance of key features.
• Address a critical research gap by employing a modern and comprehensive dataset, the ToN-IoT dataset, which reflects current IIoT attack patterns and strengthens the system’s capability to detect emerging and zero-day threats.
• Explore future enhancements by refining model architectures, experimenting with multiple CNN configurations, integrating industry-specific knowledge, and adopting advanced methods such as autoencoders and real-time attack detection mechanisms.
• Ensure continuous improvement by regularly updating the dataset and collaborating with industry experts so that the proposed AI based intrusion detection system remains effective against evolving IIoT threats.
• Investigate alternative ensemble learning techniques and additional XAI approaches to gain deeper insights and further improve the accuracy, reliability, and practical applicability of intrusion detection in IIoT networks.
SCOPE
The scope of this project covers multiple key aspects focused on designing, implementing, and evaluating an advanced AI based intrusion detection framework for securing Industrial Internet of Things (IIoT) networks. The major components of the project scope are outlined below:
- Development of IDS Framework:
The project focuses on designing and implementing an AI based intrusion detection framework tailored to the dynamic, distributed, and heterogeneous nature of IIoT networks. This includes selecting suitable deep learning models and ensemble learning strategies to accurately detect anomalous and malicious network traffic. - Integration of Explainable AI (XAI) Techniques:
A core part of the scope is the integration of Explainable Artificial Intelligence techniques to improve the transparency and interpretability of AI based intrusion detection decisions. Techniques such as SHAP (Shapley Additive Explanations) and LIME (Local Interpretable Model-agnostic Explanations) are employed to explain model predictions and highlight the contribution of individual features. - Evaluation Using ToN-IoT Dataset:
The proposed AI based intrusion detection framework is evaluated using the ToN-IoT dataset, which includes diverse real-world IIoT scenarios and a wide range of cyberattacks. This evaluation assesses the system’s capability to accurately detect, classify, and respond to various network anomalies. - Comparison with Baseline Models:
The project scope includes comparing the proposed AI based intrusion detection framework with baseline models such as Extreme Learning Machines (ELM) to measure improvements in detection accuracy, reliability, and robustness within IIoT environments. - Analysis of Results and Insights:
A detailed performance analysis is conducted to examine detection accuracy, false-positive rates, and interpretability. The insights gained from evaluating the AI based intrusion detection framework help identify strengths, limitations, and opportunities for further enhancement. - Future Directions and Recommendations:
The project concludes by outlining future research directions and recommendations, including the exploration of advanced learning techniques, optimization of model architectures, and addressing emerging IIoT security challenges to further strengthen AI based intrusion detection capabilities.
Overall, the project scope emphasizes the development, evaluation, and continuous improvement of an explainable and resilient AI based intrusion detection framework aimed at protecting IIoT networks from evolving cyber threats.
EXISTING SYSTEM
The existing system used to secure Industrial Internet of Things (IIoT) networks primarily depends on conventional security mechanisms and traditional Intrusion Detection Systems (IDSs). While these approaches provide basic protection, they face considerable limitations when dealing with complex and targeted cyberattacks in IIoT environments. Common security solutions such as firewalls, antivirus software, and access control mechanisms are largely rule-based and signature-driven, making them ineffective against advanced and unknown attack patterns.
Traditional IDSs also struggle to analyze the high-volume, heterogeneous data generated by IIoT devices, often leading to poor anomaly detection accuracy and high false-positive rates. In contrast to modern AI based intrusion detection approaches, these systems lack adaptability and fail to learn from evolving attack behaviors. Moreover, most existing IDS solutions operate as opaque “black-box” models, offering little to no explanation for their detection decisions. This lack of transparency makes it difficult for cybersecurity professionals to interpret alerts, assess system reliability, and respond effectively to threats.
Additionally, the reliance on outdated attack signatures and static rules limits the system’s ability to counter emerging and zero-day threats. Overall, the shortcomings of the existing system highlight the need for advanced, adaptive, and explainable security solutions, where AI based intrusion detection can play a crucial role in enhancing the protection of modern IIoT networks.
PROPOSED SYSTEM
The proposed system for securing Industrial Internet of Things (IIoT) networks presents an advanced framework designed to overcome the limitations of conventional security solutions and traditional Intrusion Detection Systems (IDSs). The system is built around AI based intrusion detection, combining powerful Deep Learning (DL) techniques with Explainable Artificial Intelligence (XAI) methods to improve detection accuracy, transparency, and adaptability within IIoT environments.
Unlike traditional IDS approaches that struggle with sophisticated and evolving cyberattacks, the proposed AI based intrusion detection framework employs deep learning models such as Convolutional Neural Networks (CNNs) to efficiently analyze large-scale IIoT network traffic and accurately classify anomalous and malicious activities. Training the model on the comprehensive ToN-IoT dataset, which reflects diverse real-world IIoT scenarios and attack types, enables the system to detect known and emerging threats with high reliability.
To address the lack of interpretability in existing systems, the proposed AI based intrusion detection solution integrates XAI techniques, including Shapley Additive Explanations (SHAP) and Local Interpretable Model-agnostic Explanations (LIME). These techniques provide clear insights into the reasoning behind detection outcomes, allowing cybersecurity professionals to understand feature contributions and build trust in system decisions.
By unifying deep learning–driven detection with explainable decision support, the proposed system significantly enhances IIoT security. Overall, the AI based intrusion detection framework offers a robust, transparent, and adaptive solution for protecting critical IIoT infrastructure and operations from evolving cyber threats.
WORK PLAN
The work plan is structured into multiple well-defined phases to support the systematic development and evaluation of the proposed AI based intrusion detection system. These phases include data collection, data pre-processing, algorithm design and development, testing, and performance evaluation. Each stage is carefully planned to ensure alignment with the research objectives and successful achievement of key milestones.
During the data collection and pre-processing phase, relevant IIoT network data will be prepared to support effective training and validation of the AI based intrusion detection models. The algorithm development phase focuses on designing and implementing deep learning–driven detection mechanisms capable of identifying complex cyber threats within IIoT environments.
Extensive testing and validation procedures will be carried out to evaluate the accuracy, robustness, and reliability of the proposed AI based intrusion detection approach against a wide range of ransomware attacks and other cyber threat scenarios. Performance metrics such as detection accuracy, false-positive rate, and interpretability will be analyzed to ensure system effectiveness.
Furthermore, collaboration with industry experts and key stakeholders will be incorporated into the work plan to support real-world validation and potential deployment. This collaborative approach ensures that the AI based intrusion detection system remains practically relevant, scalable, and capable of addressing real-world IIoT security challenges.
REQUIREMENT ANALYSIS AND SPECIFICATION
FUNCTIONAL REQUIREMENTS
The functional requirements of the proposed AI based intrusion detection framework for securing Industrial Internet of Things (IIoT) networks are defined to ensure effective threat monitoring, accurate detection, and reliable response mechanisms. The key functional requirements are as follows:
- Network Traffic Monitoring:
The system shall continuously monitor IIoT network traffic in real time, capturing and analyzing data packets transmitted across connected devices and sensors. - Anomaly Detection:
The framework shall employ advanced deep learning techniques, including Convolutional Neural Networks (CNNs), to analyze network behavior and identify anomalies that may indicate potential cyber threats. - Attack Classification:
Once anomalous activity is detected, the system shall classify the attack type, differentiating between various cyber threats such as Denial of Service (DoS), Distributed Denial of Service (DDoS), intrusion attempts, and other malicious behaviors. - Ensemble Learning:
The system shall use ensemble learning strategies to combine predictions from multiple deep learning models, improving the accuracy, stability, and robustness of the intrusion detection process. - Explainability:
Explainable Artificial Intelligence (XAI) techniques, including Shapley Additive Explanations (SHAP) and Local Interpretable Model-agnostic Explanations (LIME), shall be integrated to enhance transparency and enable users to understand the decision-making logic of the AI based intrusion detection system. - Real-time Alerts:
The system shall generate real-time alerts or notifications when suspicious activities or intrusions are detected, enabling timely response and mitigation by security administrators. - Integration with IIoT Devices:
The framework shall support seamless integration with heterogeneous IIoT devices and sensors to ensure comprehensive network visibility and coverage. - Scalability:
The intrusion detection framework shall be scalable to support expanding IIoT infrastructures and increasing network traffic volumes without degrading performance. - Customization and Configuration:
The system shall allow configurable detection thresholds, alerting mechanisms, and operational parameters to meet the specific security requirements of different IIoT environments. - Logging and Reporting:
The framework shall maintain detailed logs of detected anomalies, classification outcomes, and system activities to support auditing, forensic analysis, compliance, and incident response procedures.
Collectively, these functional requirements establish a strong foundation for an effective and reliable AI based intrusion detection framework capable of protecting IIoT networks from diverse and evolving cyber threats.
NON-FUNCTIONAL REQUIREMENTS
In addition to functional capabilities, the proposed AI based intrusion detection framework for securing Industrial Internet of Things (IIoT) networks must satisfy key non-functional requirements to ensure reliability, efficiency, and practical usability. These requirements are outlined below:
- Performance:
The system shall deliver high performance with minimal latency in processing network traffic and detecting anomalies, enabling timely responses to cyber threats through the AI based intrusion detection mechanism. - Scalability:
The framework shall be scalable to support the expansion of IIoT networks, efficiently handling increasing numbers of devices and higher traffic volumes without degrading detection accuracy or overall performance. - Reliability:
The AI based intrusion detection system shall operate continuously with minimal downtime, ensuring consistent monitoring and protection of IIoT infrastructure against cyber threats. - Accuracy:
The system shall maintain high detection and classification accuracy, reducing false positives and false negatives to provide dependable threat identification within IIoT environments. - Interpretability:
Explainable Artificial Intelligence (XAI) techniques shall be integrated to improve interpretability, allowing cybersecurity professionals to understand and trust the decisions generated by the AI based intrusion detection framework. - Security:
The framework itself shall implement strong security controls, including authentication, access control, and encryption, to protect sensitive data and prevent unauthorized access or tampering. - Usability:
The system shall feature an intuitive and user-friendly interface for configuration, alert monitoring, and report generation, enabling efficient use by security analysts and administrators. - Adaptability:
The AI based intrusion detection framework shall be adaptable to evolving attack techniques by supporting regular updates to detection models, threat patterns, and XAI components. - Compliance:
The system shall comply with relevant cybersecurity standards and regulations such as GDPR, NIST, and ISO/IEC 27001 to ensure lawful and secure handling of IIoT data. - Resource Efficiency:
The framework shall optimize the use of computational resources, including CPU, memory, and network bandwidth, to minimize operational costs while maintaining high performance.
By meeting these non-functional requirements, the proposed AI based intrusion detection framework ensures robust, transparent, and scalable protection for IIoT networks while supporting operational efficiency and regulatory compliance.
HARDWARE REQUIREMENTS
- Processor: Intel Family
- Version: Core i5 and Higher
- Hard Disk: 500GB and more
- RAM: 16GB
SOFTWARE REQUIREMENTS
- Language: Java, Python, Solidity
- Operating System: Windows 10
- Tool: NetBeans IDE, Jupiter Notebook, Remix IDE, Ganache
- Database: MySQL
DESIGN
ARCHITECTURE DIAGRAM
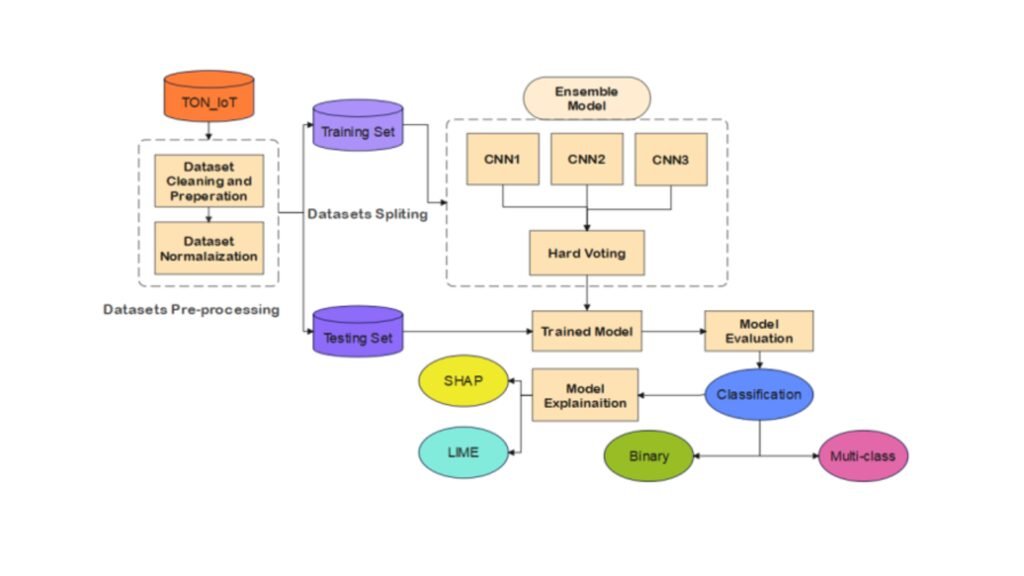
CONCLUSION
This research presents a comprehensive and effective framework for AI based intrusion detection specifically designed to address the complex and dynamic security requirements of Industrial Internet of Things (IIoT) networks. The proposed methodology leverages the ToN-IoT dataset, which captures a wide range of real-world IIoT scenarios and attack patterns, thereby addressing the continuously evolving nature of cyber threats.
The key strength of the proposed AI based intrusion detection framework lies in its intelligent integration of advanced deep learning techniques. By combining Convolutional Neural Network (CNN) models with a novel ensemble strategy, the system achieves detection accuracy exceeding 99%, demonstrating its strong capability to accurately differentiate between normal and malicious network behaviors. This highlights the robustness and effectiveness of the proposed solution in safeguarding IIoT environments.
Beyond high predictive performance, the framework significantly improves transparency and interpretability through the integration of Explainable Artificial Intelligence (XAI) techniques. The use of SHAP and LIME within the AI based intrusion detection framework enables stakeholders to clearly understand the reasoning behind model decisions and the contribution of individual features. This level of transparency enhances trust, supports informed decision-making, and enables continuous improvement of system performance and adaptability.
Moreover, this study addresses a critical research gap by utilizing the modern ToN-IoT dataset, which reflects the current IIoT threat landscape and includes a broad spectrum of attack types. Moving away from traditional datasets enhances the ability of the AI based intrusion detection system to detect emerging threats and novel attack strategies.
Future work may focus on refining model architectures, exploring diverse CNN configurations, and incorporating domain-specific industry insights to further enhance detection accuracy. Advanced approaches such as autoencoders and real-time monitoring can strengthen defenses against sophisticated attacks. Improvements in interpretability through feature selection, deployment across diverse IIoT environments, and hybrid models combining CNNs with other techniques may further improve system understanding. Additionally, advancements in XAI methods can support non-technical users in interpreting AI based intrusion detection outcomes. Continuous dataset updates and collaborative research efforts will remain essential to ensure long-term effectiveness against evolving cyber threats.


